
It’s a two-fer on a Monday! Quick update for a couple of zero-day remote code execution CVEs discovered in Mozilla Firefox. On the AX Blog, our Technical Marketing Engineer,
From the blog: “Mozilla released an out-of-band patch for Firefox that addresses two critical vulnerabilities (CVE-2022-26485 and CVE-2022-26486). Both are actively exploited in the wild as zero-days. Both are use-after-free issues in the browser’s XSLT processing and WebGPU IPC frameworks, respectively...Given this is an actively exploited zero-day, it’s recommended that IT admins prioritize patching this vulnerability within 24 hours to reduce exposure to malicious actors.
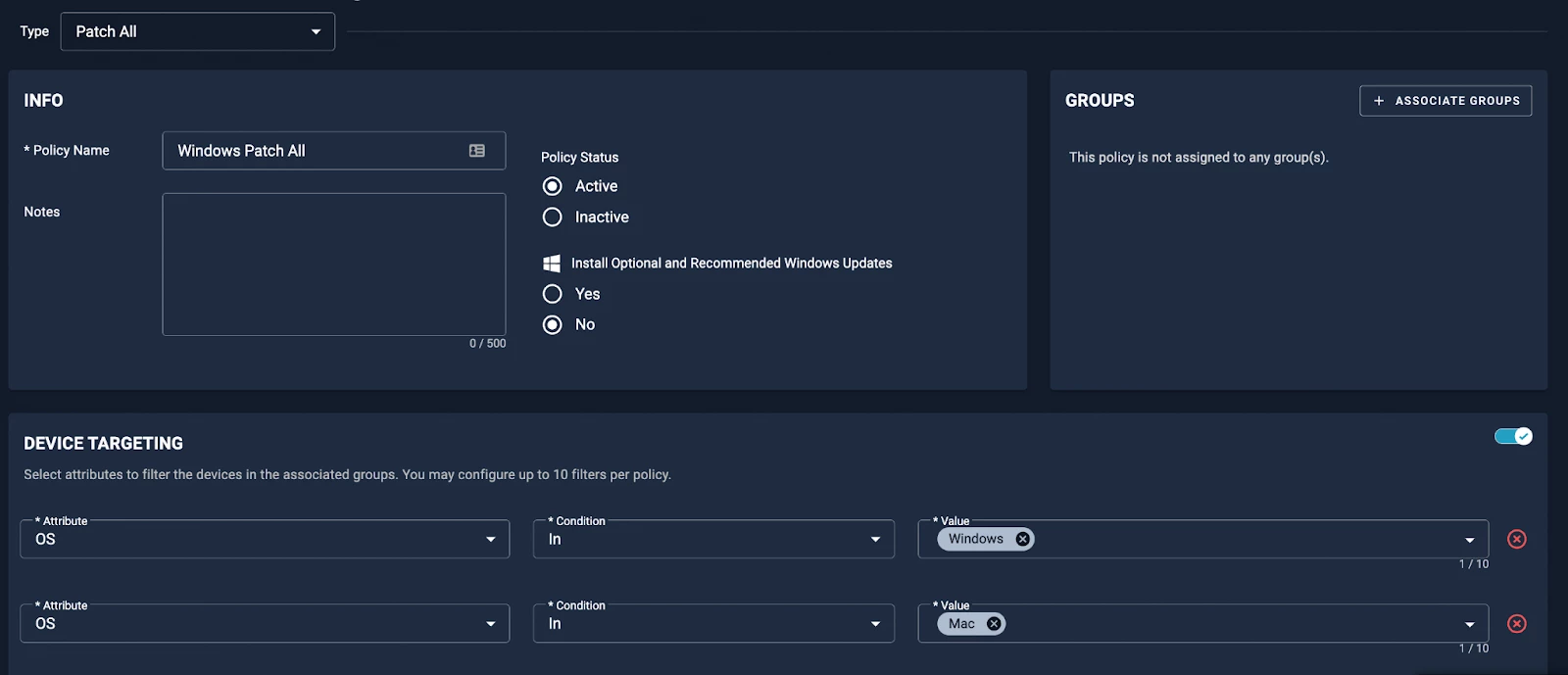
For Firefox, Firefox ESR, and Thunderbird, you can fix vulnerabilities fast with Automox by using a patch-all policy for Windows and Mac (which will patch every third-party software we support on these OSes). Patch all policies ensure you fix vulnerabilities fast in the most common and highest risk applications in your environment.
We recommend you set up these policies on a recurring schedule to eliminate your immediate and future risk, as not all distributions have released patches as of Monday morning.” (See below)
If you have any questions/concerns/feedback, let us know in the comments or contact us at communit@automox.com.
