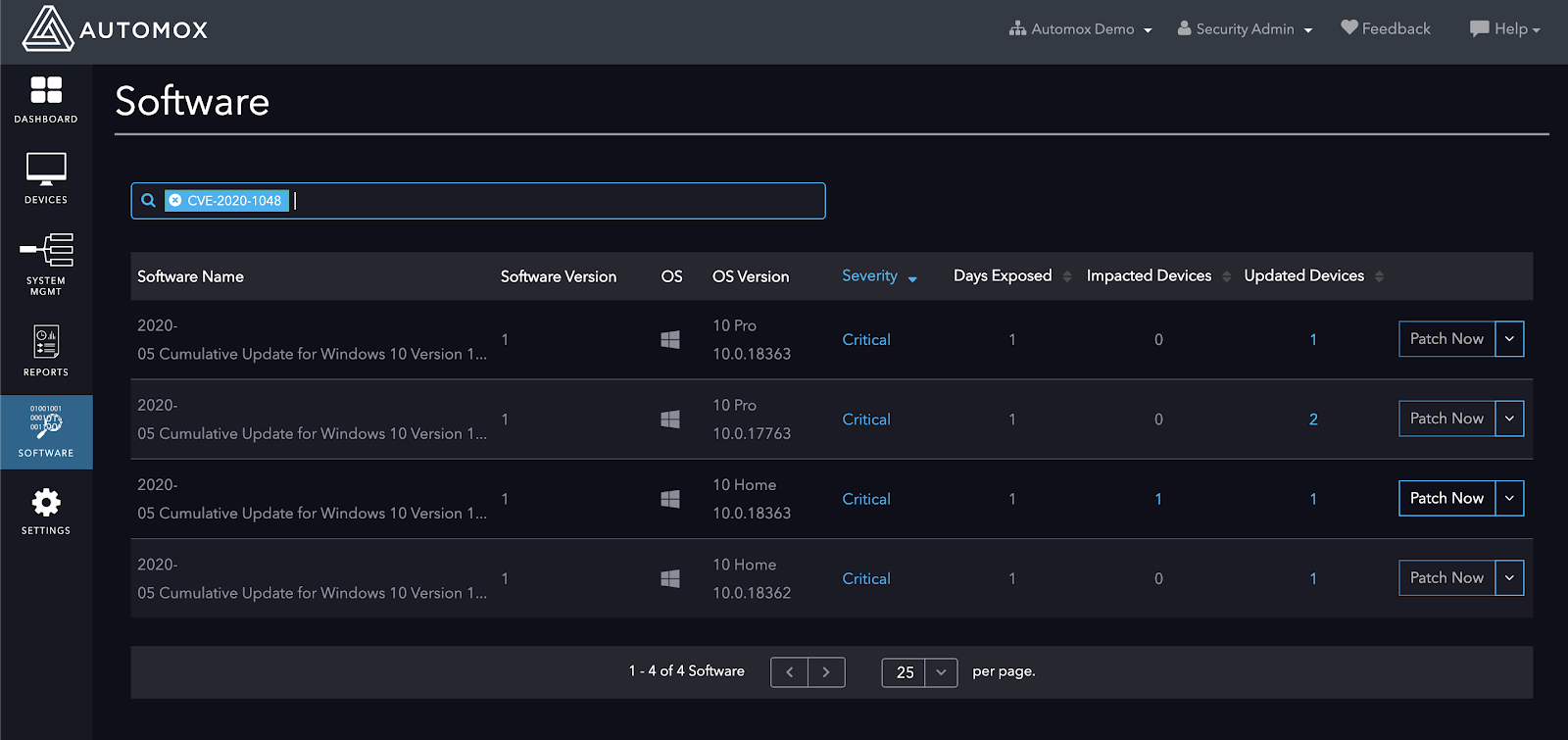
The best way to remediate this vulnerability immediately across your entire organization is to use the Software dashboard located in the console.
From the Software dashboard, search for CVE-2020-1048 to identify all of the software that needs to be patched in order to fully remediate the CVE within your organization.
As you can see from the screenshot above, CVE-2020-1048 has devices that do not have the latest update installed. To remediate, simply click on the ‘Patch Now’ button located on the right-hand side of each software package:
Note: Performing the above steps will not automatically reboot the devices, just install the patch on the OS. A reboot might be required depending on the current state of the device. To determine if a device needs a reboot after the patch is applied, perform the following actions in the console:
- Click on the number under “Impacted Devices”. This will take you to a list of devices that the patch was applied to when you clicked “Patch Now”.
- Once the device finishes updating, select all the devices in the list and click “Rescan” to determine if a reboot is needed.
- After the rescan, a device that needs a reboot will be in “Needs Reboot” status.
- Select just those devices and click “Reboot”.
- When the device comes back online, the patch will be fully installed.