Hello, I am facing error in policy scheduling. When we create the worklets, we leave the execution scheduled, but the execution does not occur. If we perform the execution manually, the policy applies normally, but the scheduling does not occur.
In this case, we have two situations.
Situation 1:
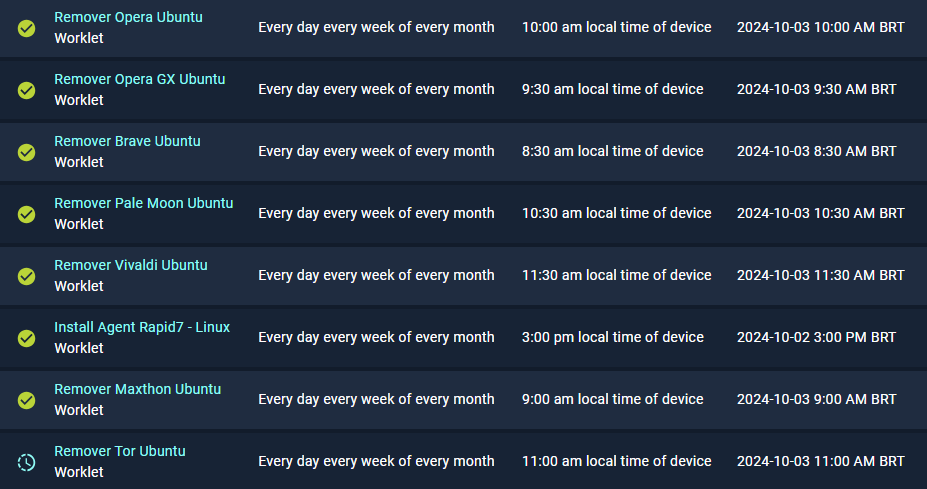
We created 3 months ago 5 policies to remove specific browsers from linux machines. The policies work perfectly if executed manually, but if we schedule, only 1 of them is executing correctly. All are add in the same group and running at alternate times.
Situation 2:
We create a policy to add a mandatory software and if we run it manually, it works correctly, but we schedule the execution and the policy does not run. We have already changed it from one group to another, from one machine to another, from one to another
Are we doing something wrong? Has anyone experienced this?