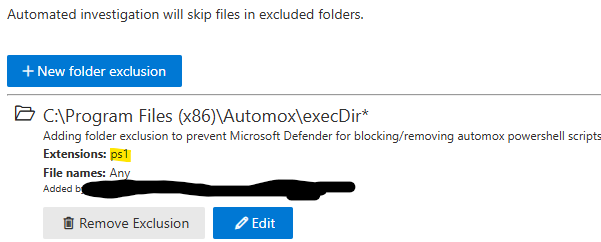
Hi all,
Does anyone know if Automox has any recommended Microsoft Defender exclusions please? We use Microsoft Defender for Endpoint and want to ensure we’re not impeding on Automox performance / usability at all please. Further, if anyone knows of any local client firewall rules (other than the 7844 for Cloudflare Tunnels) that might be needed please.
I tried to search but I can’t seem to see anything, so thought I’d best double check.
Thanks in advance!