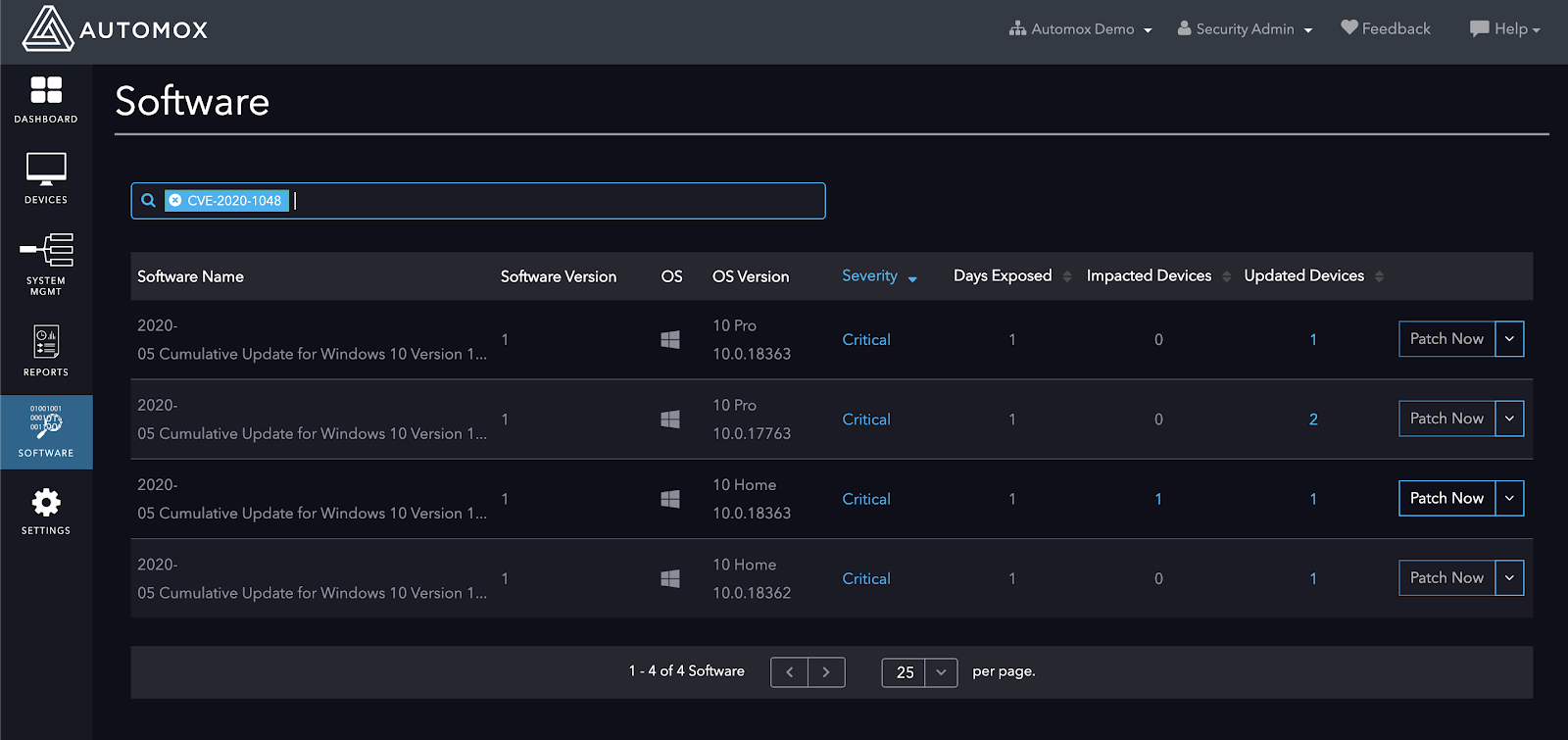
https://windows-internals.com/printdemon-cve-2020-1048/
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1048
This vulnerability has been weaponized and is now widely available. If exploited, it will install a persistent backdoor that will not remediate even after a patch.