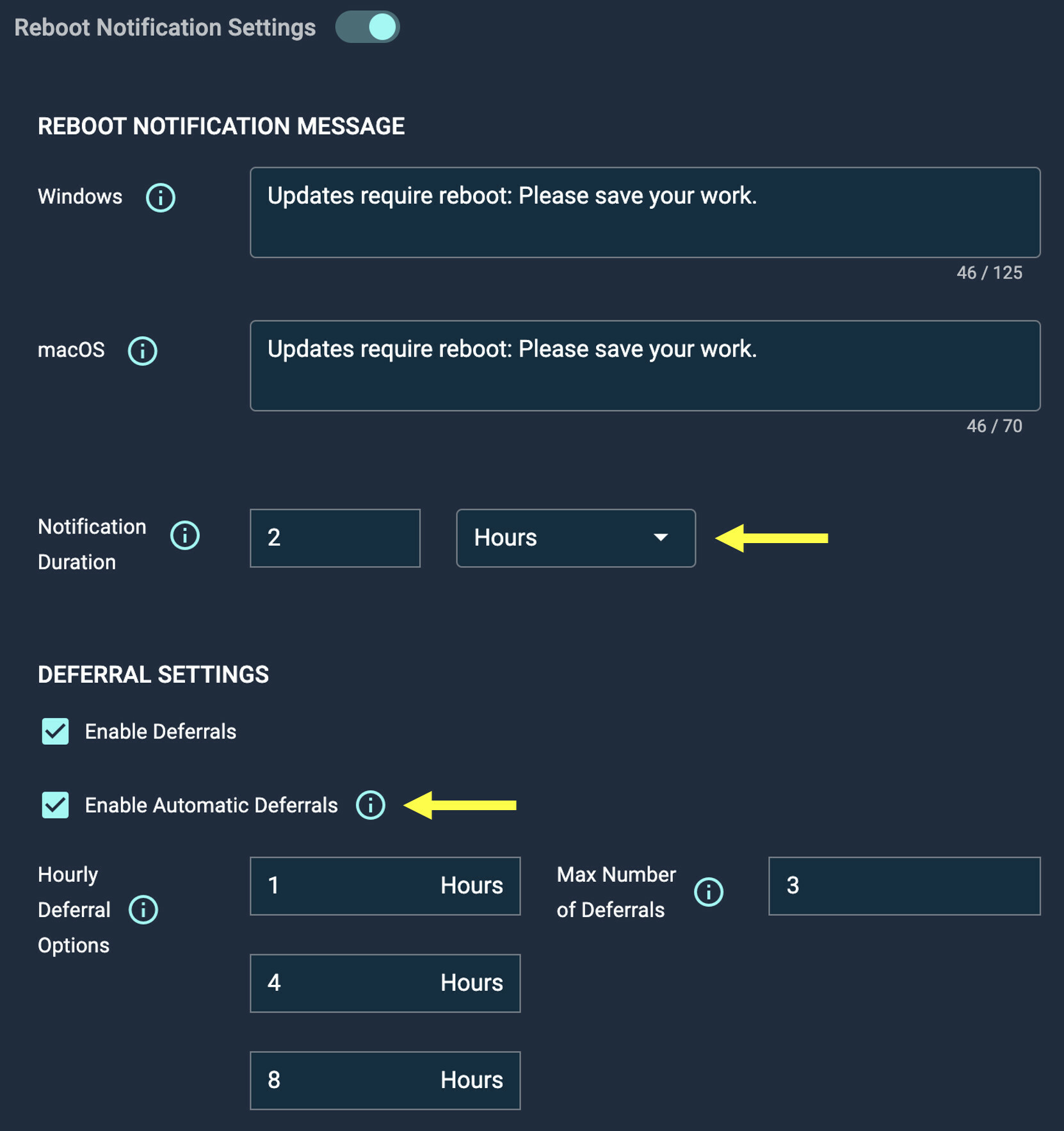
Today we released two new patch policy features to give admins even more control over end user notifications:
Customizable Reboot Notification Length
Admins can now customize the length of time that a reboot notification is displayed to the user, from 15 minutes up to 8 hours.
Automatic Reboot Deferrals
Admins can now enable automatic reboot deferrals when end users do not acknowledge the reboot notification at all.
One of the user’s available deferrals will be automatically consumed on behalf of the user until they are out of deferrals. Automox will choose the longest available deferral time.
Once a user is completely out of deferrals, their machine will restart instead.