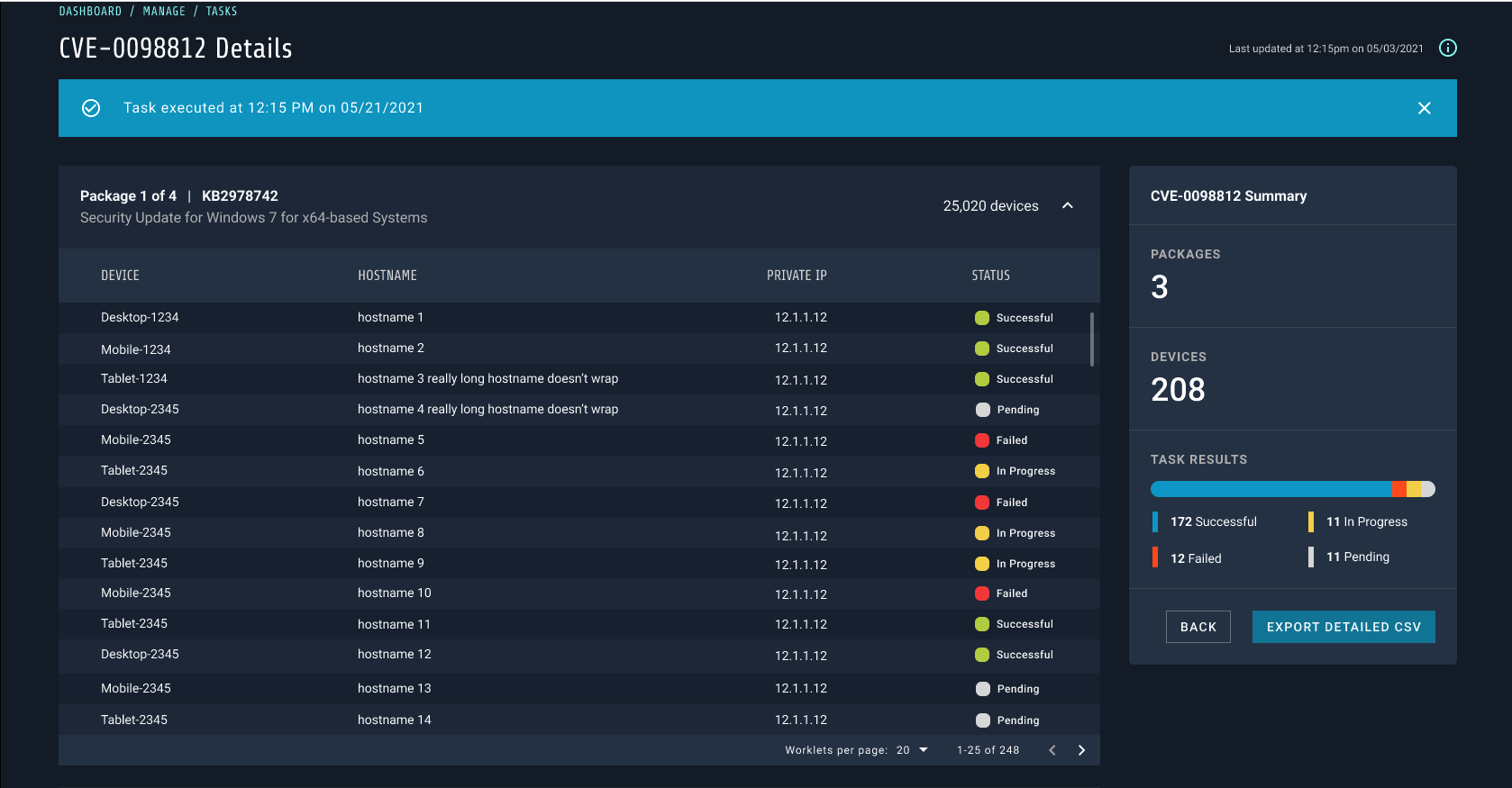
At the core of any successful vulnerability management remediation process is an alignment of competent resources, security best practices, and continuous assessment. With cyberattacks becoming an ever-growing part of our daily lives, it’s important that organizations put a functional vulnerability management remediation process in place.
But first, we should ask the question, what exactly is vulnerability management? Well, in ideal circumstances, you can plan for the following items:
-
Cyber Security Governance outlines executive management’s strategic direction in setting scope, remediation cycle, term objectives, budget, and realistic expectations of performance as negotiated with stakeholders.
-
Cyber Security Strategy that defines roles, responsibilities, prioritizations of what is critical or required to protect for both business continuity and legal reasons such as regulatory compliance needs.
-
Program Solutions such as vulnerability management scanners to enumerate vulnerabilities of configuration and patching levels.
With this in mind, you can now define a process. Although many groups exist with varying viewpoints, there are some key elements that each process has in common:
- Assess Vulnerabilities
- Prioritize Findings by Impact
- Action on Findings
- Re-assess and Validate Progress
- Report Metrics/KPIs
With this community post, I just barely scratched the surface of this topic. Our team has included a wealth of knowledge in our blog post here, but I want to hear from y’all! Have you implemented a vulnerability management remediation process? If not, is it something you’d like to do?