Good morning,
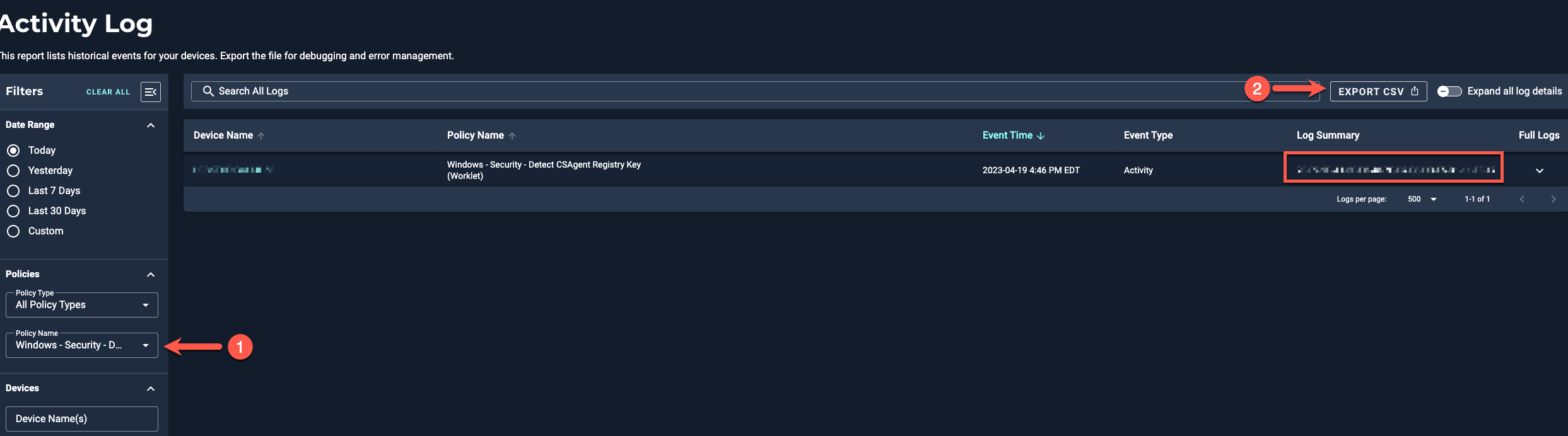
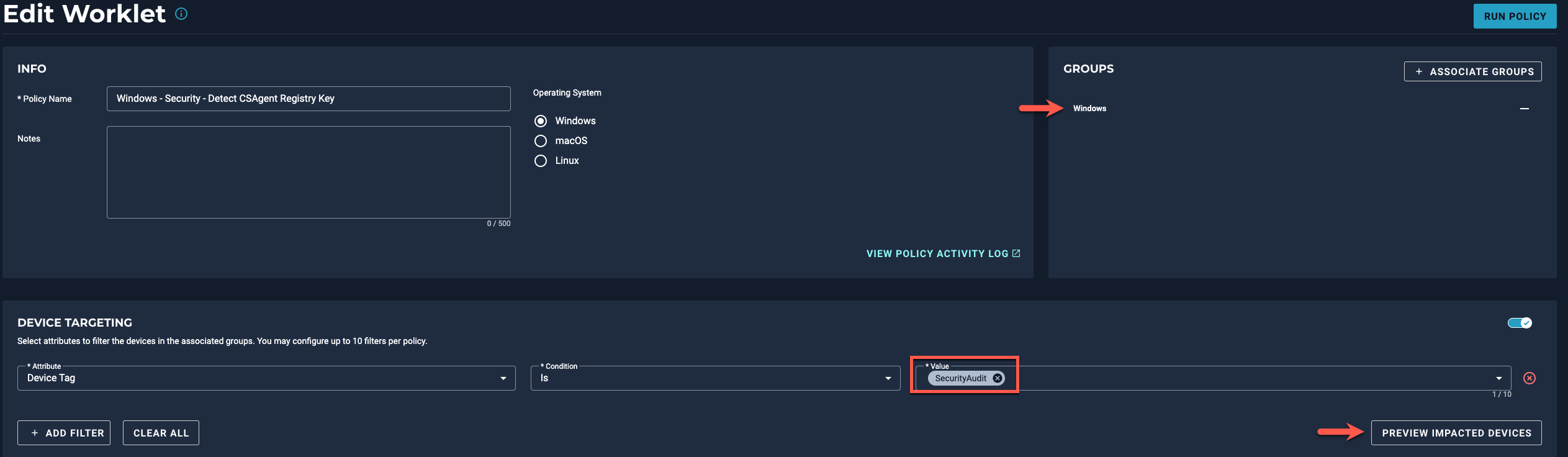
We direly need your assistance, and this is really time sensitive as it deals with our Antivirus software (Crowd Strike). In a nutshell, we have Crowd Strike installed on our environment, but it is managed by parent corporate Sec Ops team. Just recently they reported not seeing 484 Hosts on the console, and needed us to remediate the issue. As per their team, to remediate we would need a special key from the registry per host, and provide those keys to Sec Ops team. They will then provide a token key to uninstall Crowd Strike. Then installation would be via Automox, which we have already scripted and available.
Our issue is scripting an API that could pull registry entries from all of our hosts along with the hostname, and putting them on a table format. If there is any help you can provide in creating the API script it would be helpful.