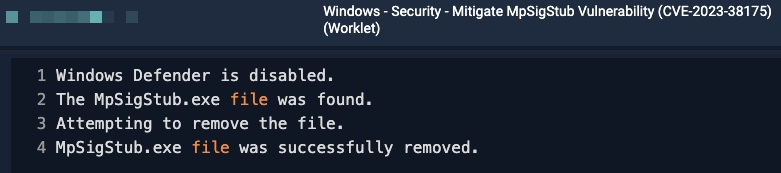
I’m trying to remediate https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-38175
We use a 3rd party antivirus and not Microsoft Defender. Microsoft recommends deleting the file MpSigStub.exe. It’s located in C:\Windows\System32.
I tried to create the following but i think it’s not working because system32 needs elevated privileges. Any ideas?
Evaluation Code:
Exit 1
Remediation code:
Remove-Item -path "C:\Windows\System32\MpSigStub.exe”