Here’s an example of a worklet we recently created in response to managing updates for the BlueKeep vulnerability:
Introducing the Automox Worklet
To enable your ability to configure and update systems using the Automox platform, we’ve created an endpoint hardening worklet that disables the remote desktop protocol connection.
An Automox worklet is an open extensible automation architecture that allows IT operations to create any custom task that they can imagine. Our tool consumes and contains these worklets within a policy that can be automated and maintained across all devices with the Automox sensor installed. These reusable units of work can be applied across any supported operating system (including Windows, Linux, and OSX) and are powered by PowerShell and Bash scripting.
How to Disable Remote Desktop Services Worklet
If a machine is unpatchable, security administrators can use this worklet as a mitigating control to protect impacted Windows systems from the BlueKeep vulnerability. This worklet also can act as a general security hardening on all Windows devices with newer operating systems not vulnerable to the specific threat.
To deploy this endpoint hardening worklet, do the following:
-
Log in to your Automox Console.
-
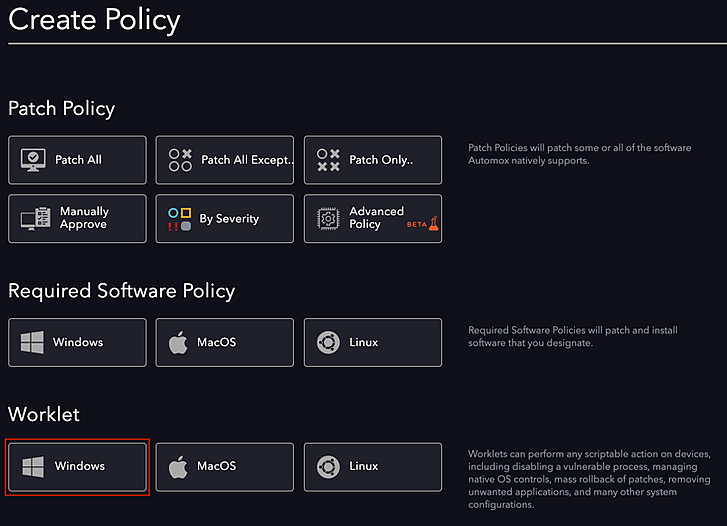
Browse to the System Management page and click Create Policy .
-
Choose Windows under Worklet
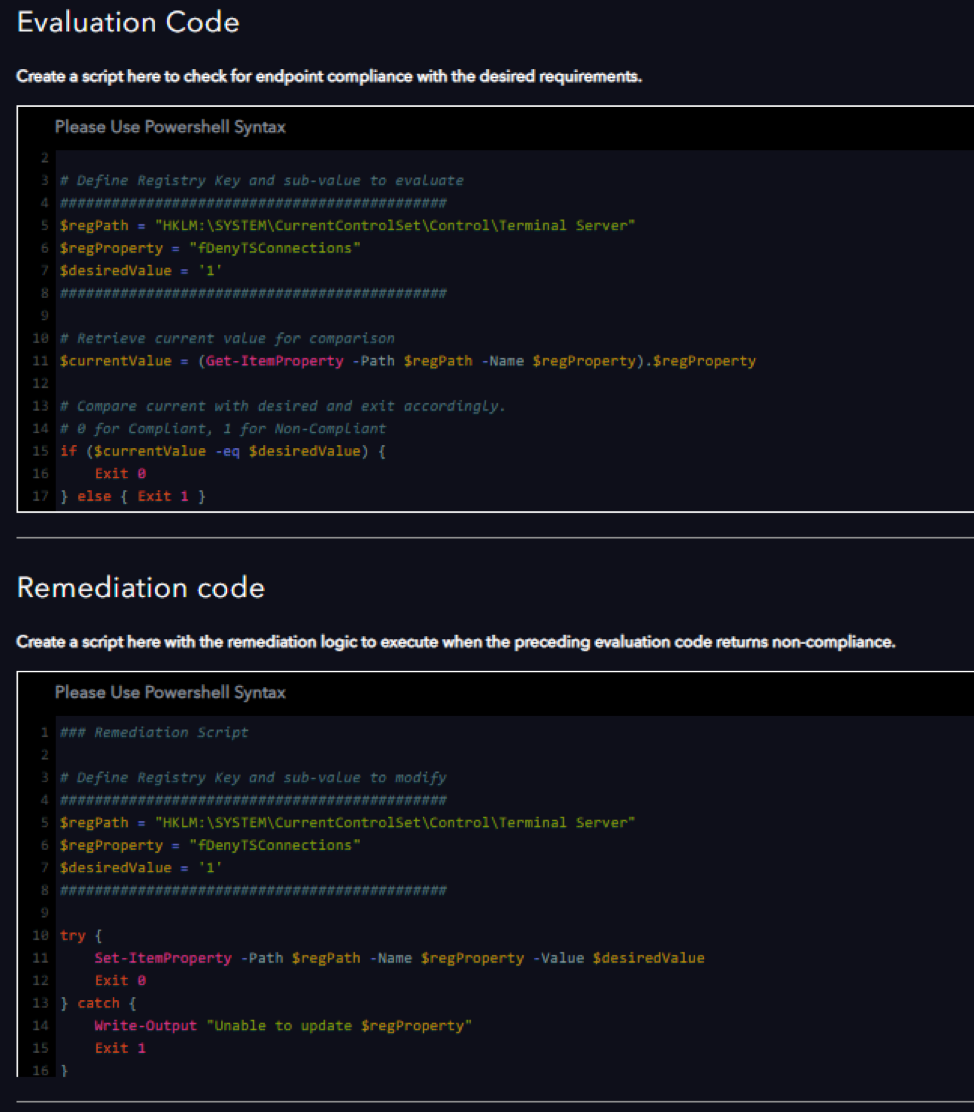
- Insert the Evaluation and Remediation Code scripts. The evaluation code keeps you apprised of each device’s ongoing compliance, as well as flags the device for remediation. The remediation code enforces this setting on the schedule you define.
• Under Evaluation Code:
# Define Registry Key and sub-value to evaluate
#############################################
$regPath = "HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server"
$regProperty = "fDenyTSConnections"
$desiredValue = '1'
#############################################
# Retrieve current value for comparison
$currentValue = (Get-ItemProperty -Path $regPath -Name $regProperty).$regProperty
# Compare current with desired and exit accordingly.
# 0 for Compliant, 1 for Non-Compliant
if ($currentValue -eq $desiredValue) {
Exit 0
} else { Exit 1 }
• Under Remediation Code:
# Define Registry Key and sub-value to modify
#############################################
$regPath = "HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server"
$regProperty = "fDenyTSConnections"
$desiredValue = '1'
#############################################
try {
Set-ItemProperty -Path $regPath -Name $regProperty -Value $desiredValue
Exit 0
} catch {
Write-Output "Unable to update $regProperty"
Exit 1
}
Originally posted on the Automox blog here.