Hi, everybody - Chad here. We’re all extremely stoked to announce the release of Vulnerability Sync! This feature will help to dramatically reduce the time required to remediate vulnerabilities from days/hours (across multiple teams) to minutes, with a single click from one operator. Vulnerability Sync provides actionable insights based on data from Technical Partners including CrowdStrike, Rapid7, and Tenable that help IT teams quickly identify, analyze, prioritize, and remediate vulnerabilities.
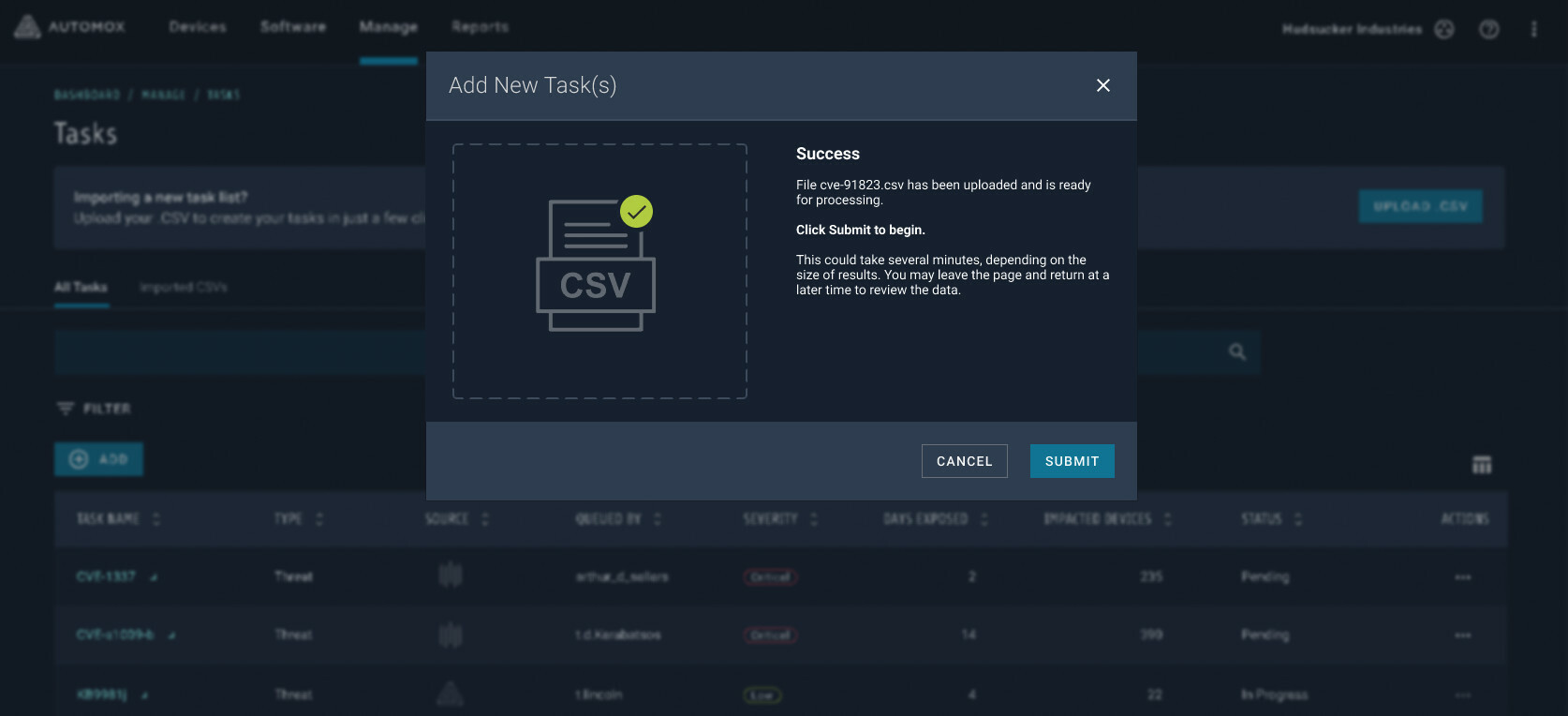
In short, you’ll download a vulnerability report from a 3rd-party scanner, then upload that into the AX console. You’ll need to make sure the report lists hostnames and CVE IDs, as these are crucial to the sync. Then, simply upload the CSV file: