Well, what would a Monday morning be without some vulnerabilities to talk about? Over on the Automox Blog,
From the AX blog: “Dirty Pipe is a vulnerability in the Linux Kernel disclosed Monday morning. Dirty Pipe, or CVE-2022-0847, allows overwriting data in arbitrary read-only files. This can lead to privilege escalation and code injection into root processes. The vulnerability exists in all Linux kernel versions from 5.8 forward and has been patched in Linux 5.16.11, 5.15.25, and 5.10.102….Given the prevalence of Linux in highly sensitive infrastructure, this is a very important vulnerability to mitigate. It is highly recommended that IT and SecOps admins prioritize patching and remediation of this vulnerability in the next 24 hours to reduce organizational risk from this vulnerability.”
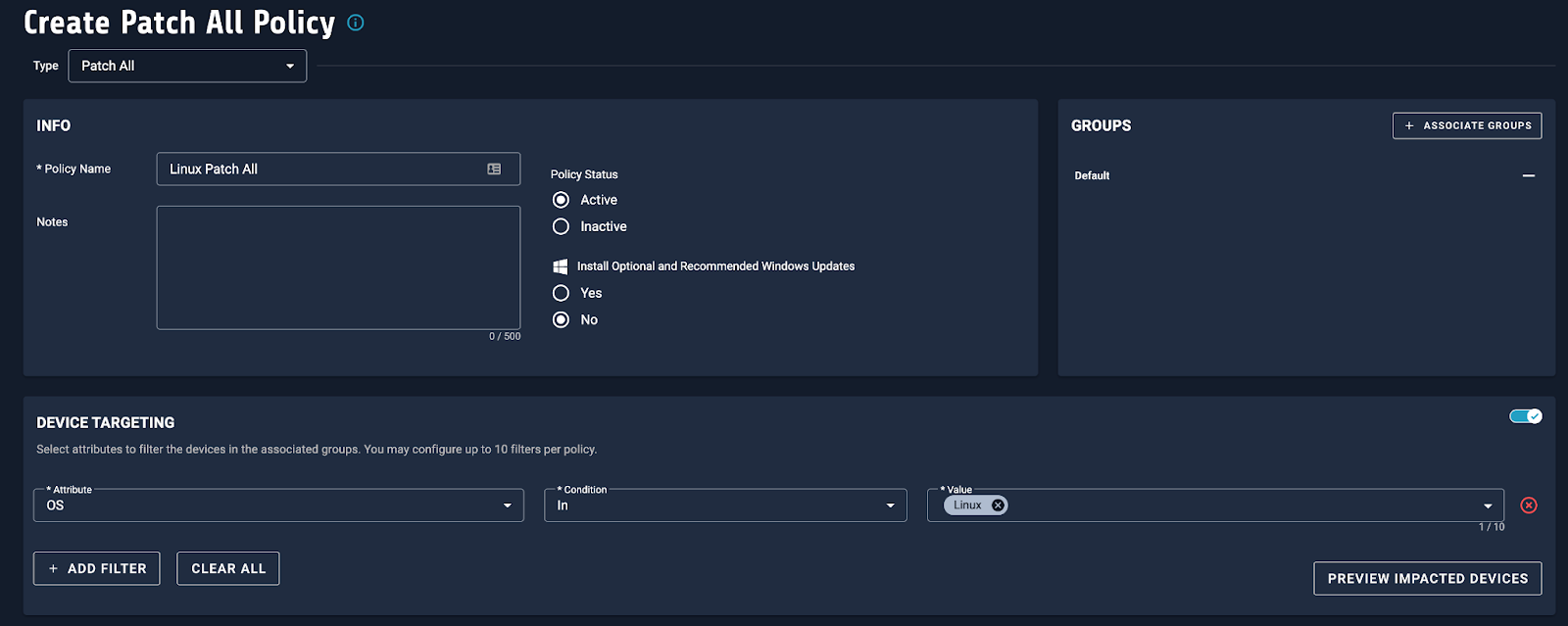
Remediation steps: If you don’t have an existing Linux patch policy, we recommend a Patch All policy with device targeting for Linux OSes (this will also patch Linux third-parties we cover) to fix this vulnerability fast – ideally within the next 24 hours. See below: