Automox provides some great insight around patch installations triggered by Automox. You can find those details in the Activity Log report, and you can see patches are Installed or Awaiting Update in the console.
Well, what do we know about patching details outside of the Automox policies? There are times we want more detail around patches that are installed manually, or through another method.
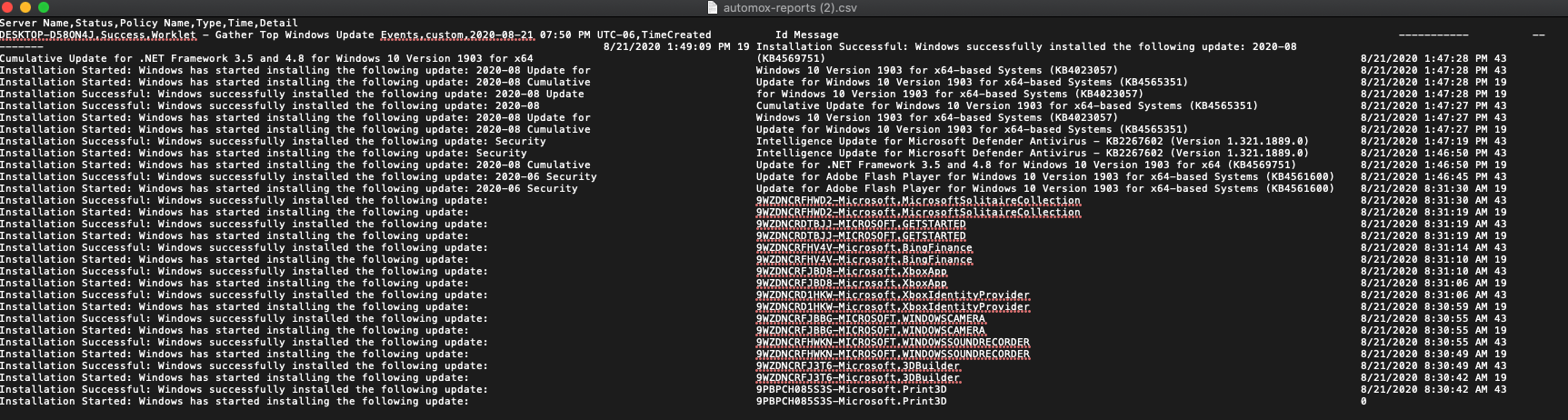
Here is a Worklet that will collect Events generated by the Windows update client. Centralizing this information into the Activity log can save a good amount of time as you will not have to connect to different devices to see the details.
Currently you can define the timeframe and eventIDs to include. I would love feedback to see what else everyone else would like to include.
Remediation Code:
######Modify values to fit your needs######
$WUeventIDs = 19,20,21,43
$DaysOfLogs = 1
###########################################
#Collect Events and write output to Activity Log
$timeSpan = (Get-Date) - (New-TimeSpan -Day $DaysOfLogs)
$UpdateEvents = Get-WinEvent -Provider Microsoft-Windows-WindowsUpdateClient | Where-Object {$_.id -iin $WUeventIDs -and ( $_.TimeCreated -ge $timeSpan )}| Format-Table TimeCreated,id,message -Wrap
Write-Output $UpdateEvents
Exit 0
The collected information is added to the Activity Log, and can be exported as a CSV. Here is what it looks like after exporting the CSV: