Welcome back to another week of security news and updates! Not surprisingly, we’re seeing more from the Microsoft Exchange situation and… another Chrome flaw. Check out the stories below -
Microsoft releases mitigation tool for on-premises Exchange servers
Microsoft’s new one-click Exchange On-Premises Mitigation Tool is now available and built as an interim integration for those that are either not familiar with the patching process or haven’t yet applied the Exchange security updates released on March 2nd. Roughly 82,000 servers remain vulnerable to the exploits. Microsoft has been clear that this is not supposed to be a replacement for the Exchange Server security update, but is to serve as a way to defend against the highest risks until they are able to patch the flaws. Downloading the tool will automatically mitigate CVE-2021-26855 with a URL rewrite configuration, run a malware scan, and reverse changes made by identified threats, Microsoft says.
Six hacking groups suspected of using the zero days pre-patch
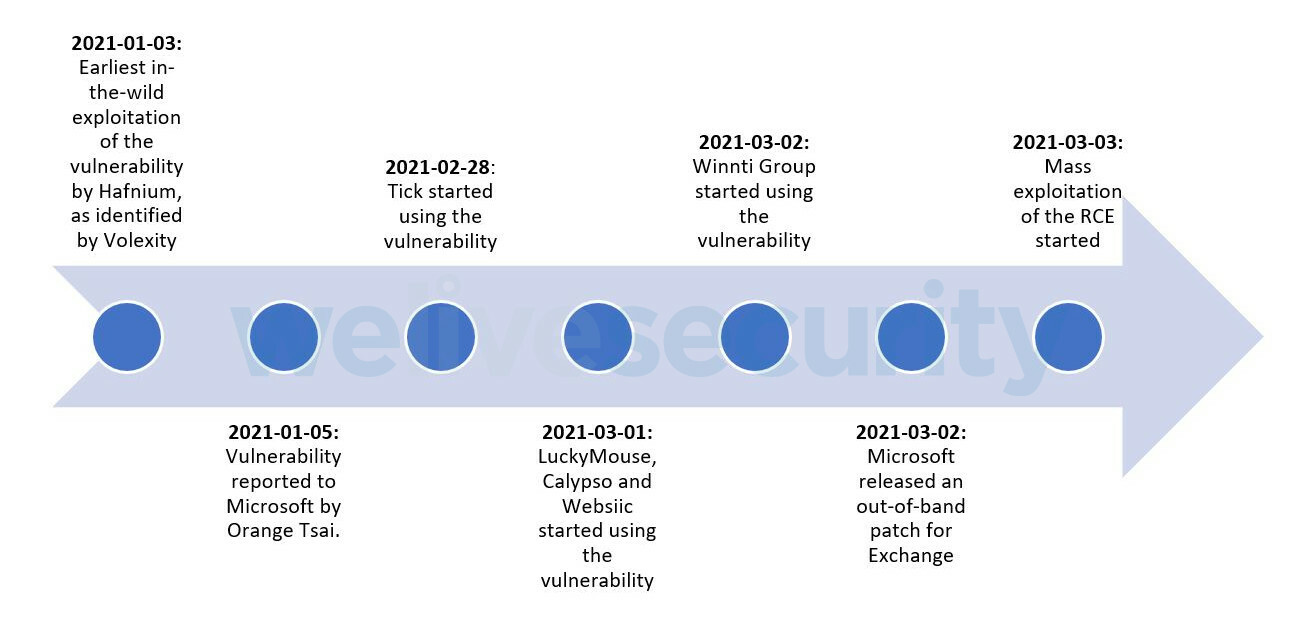
Speaking of Microsoft’s Exchange troubles… it looks like the exploitation of critical Exchange flaws could be much worse than originally predicted. An analysis by Slovak security shop ESET claims that six advanced criminal hacking groups, thought to have some level of state sponsorship, used the zero days to attack government and industry sites before the flaws were patched. Previously, Microsoft claimed that only one Chinese-based hacking group, Hafnium, had exploited the code. These additional groups include Tick, LuckyMouse, Calypso, Websiic, and the Winnti Group. Here’s the timeline provided by ESET:
Linux kernel flaws from 2006 could deliver root privileges to attackers
Three recently unearthed vulnerabilities in the Linux kernel, located in the iSCSI module used for accessing shared data storage facilities, could allow root privileges to anyone with a user account. These vulnerabilities are listed as CVE-2021-27363, CVE-2021-27364 and CVE-2021-27365. The flaws have lived in the Linux kernel code without detection until GRIMM researchers discovered them. On the bright side, the code is not remotely accessible, but it’s still important to take care of the flaw ASAP. The bugs have been patched in the following kernel releases: 5.11.4, 5.10.21, 5.4.103, 4.19.179, 4.14.224, 4.9.260, and 4.4.260.
Google warns Mac, Windows users of Chrome zero-day flaw
And we’re back with another Google Chrome zero-day flaw! If it feels like we’re talking about Google Chrome a lot, this is the third zero-day flaw to be disclosed by Google in the past three months. If exploited, the flaw could allow remote code-execution and denial-of-service attacks on affected systems. The vulnerability exists within Blink, the browser engine for Chrome developed as part of the Chromium project. The flaw (CVE-2021-21193) ranks 8.8 out of 10 on the CVSS vulnerability-rating scale, making it high-severity. Specifically, the flaw is a use-after-free vulnerability, which relates to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program, according to a description of the vulnerability.
Any security updates from your end? Share them below!