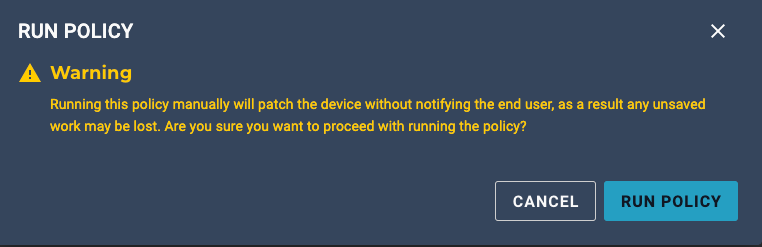
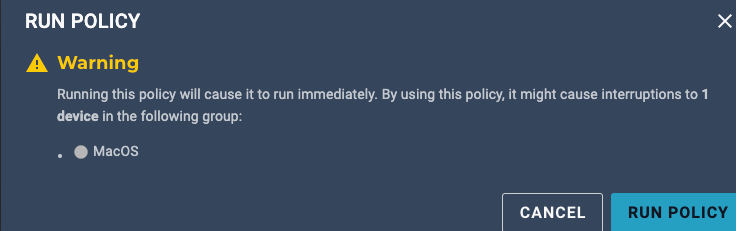
UPDATE: I just discovered Automox will always run Remediation when the policy is run manual - this is an extremely aggravating feature which makes testing evaluation code much more difficult. My question to the Automox staff - doesn’t this do more damage than good, what is the actual purpose of this? This makes testing policy very tedious, just like how running a policy manually will not display notifications the same as when run via schedule. Something this impactful should be a warning on the worklet, not buried in documentation! Please include something like the below as this causes such an unbelievable headache
It appears the worklet evaluation block (Windows) either doesn’t work, or I’m doing something wrong…
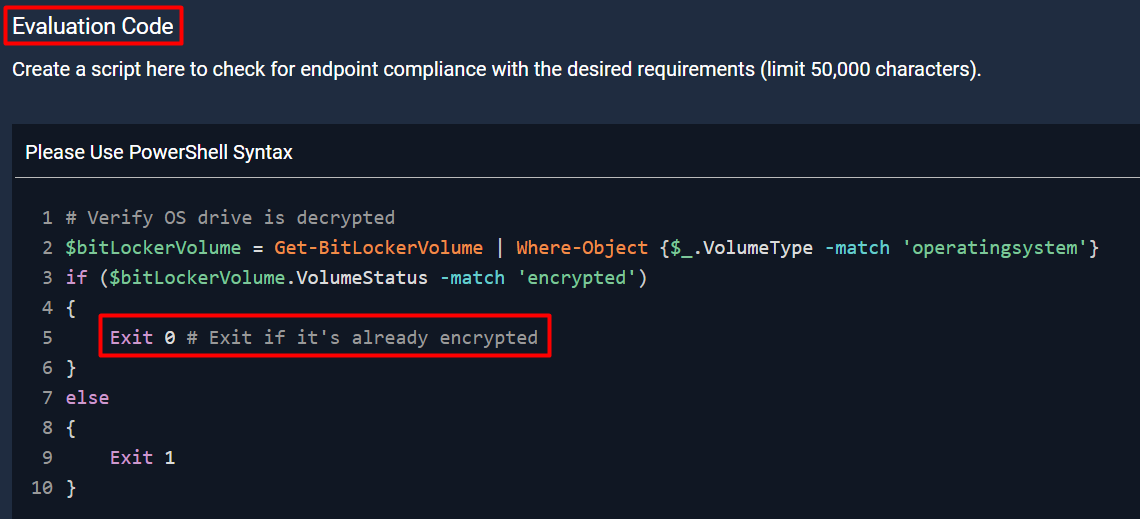
I’m building a BitLocker worklet and exit code 0 in the evaluation block will always run the remediation block. According to the documentation, exit code 0 is meant to mark as compliant and exit code 1 is meant to trigger remediation, but clearly this is not the case.
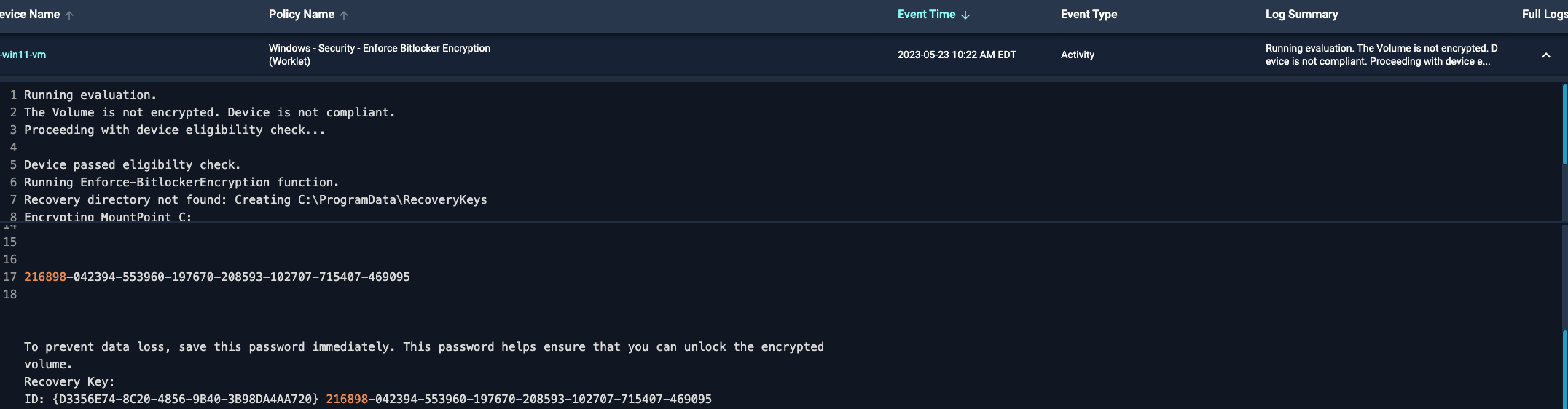
See example below - I put the exact same condition in the remediation block that I put in the evaluation block, and it continues to remediation block and exits with exit code 0 there, but will not exit with exit code 0 in the evaluation block (the Write-Output in the activity log proves it’s always going to the remediation block).
Evaluation block:
Same condition in the remediation block except with a Write-Output:
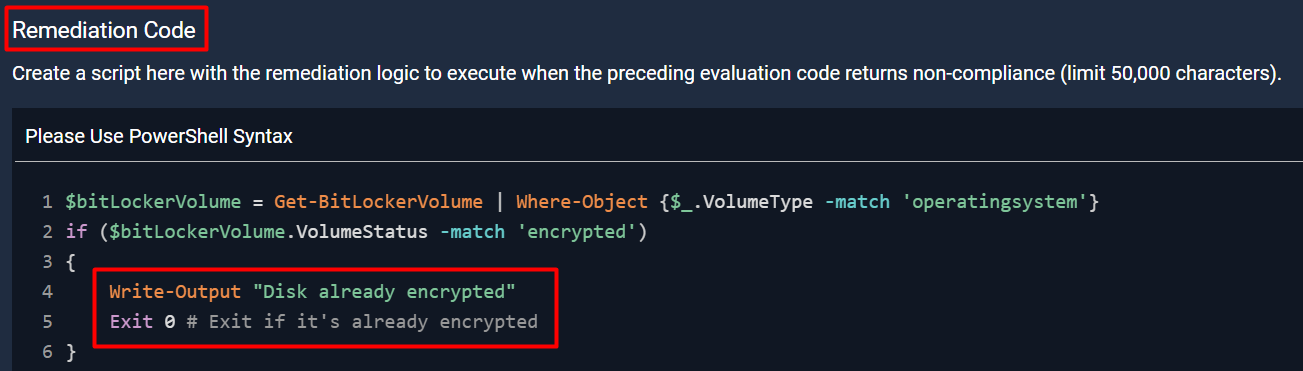
Activity logs proving that it’s always being marked as requiring remediation and running in the remediation block (because the Write-Output is displaying):
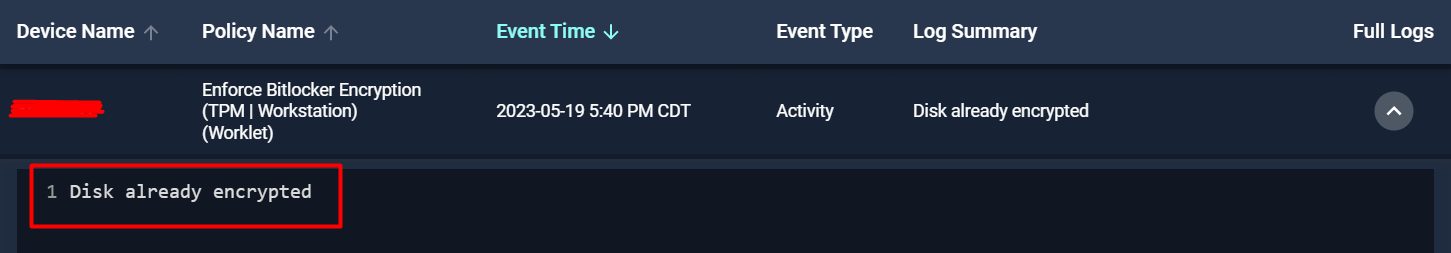
Because the evaluation block is so unreliable, it seems I have to put all my conditions in the remediation block where exit codes are working properly - this is extremely inconvenient. Also yes, the device in the screenshot is my test machine where the script returns the condition as expected when run locally. I’m just glad I caught this before rolling this out to any production, as allowing remediation to run regardless of exit code in evaluation, would’ve led to some extremely unfortunate circumstance.
Best answer by JohnG-Automox
View original